Monitor the Security and Compliance of Vendors, Clients, and Partners
360° Assessments
Inside, outside, and independent cyber risk perspective
Compliance
Automated continuous tracking and monitoring
Network Security
Rating updates and vulnerability alerts in real-time
Hacker Threat Analysis
See what hackers are saying about your vendors
Breach Monitoring
Track breaches and remediation responses
All about iTrust
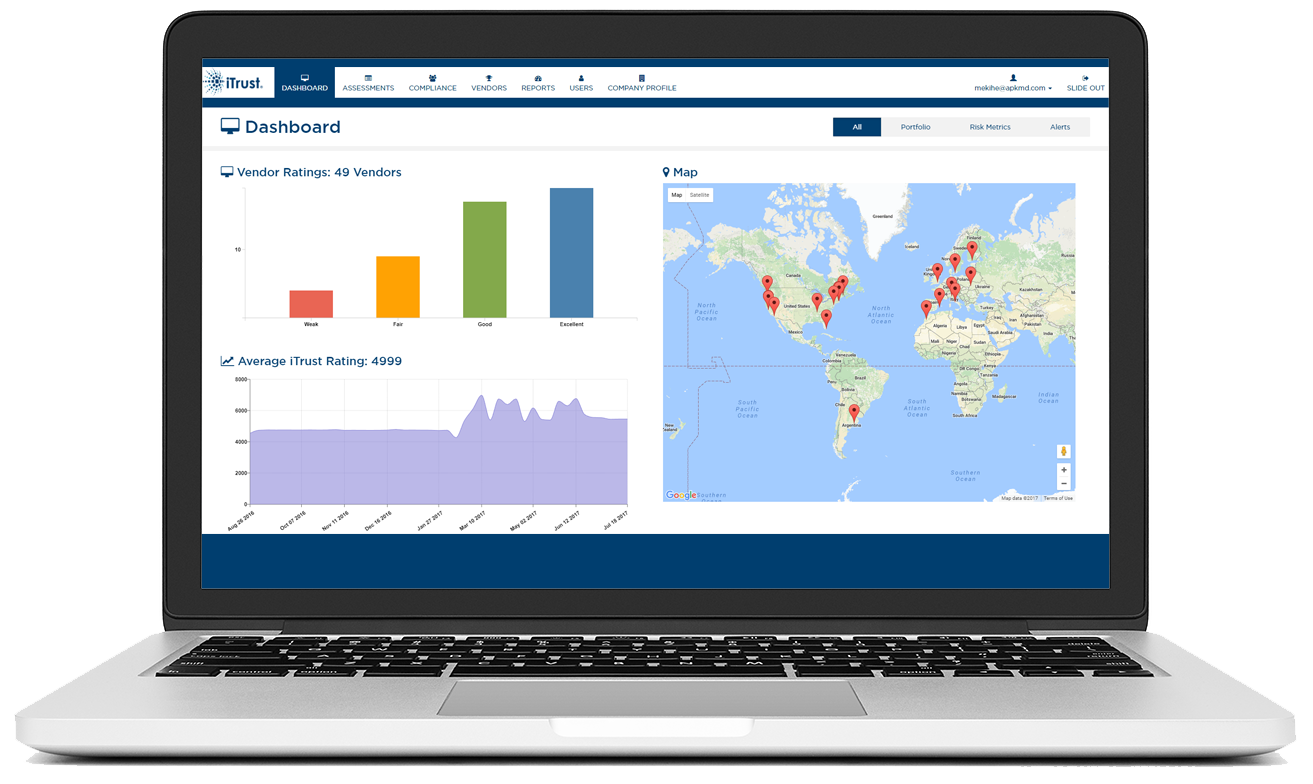
What is iTrust?
iTrust is an all-in-one platform with the essential risk management capabilities your business needs. Managed from a single pane of glass, iTrust’s advanced algorithms are designed to deliver the most intelligent analysis of security and compliance risks with real-time alerts and time boxed metrics.
What is an iTrust Rating?
An iTrust Rating provides insight into a company’s vendor security ratings and compliance. An iTrust Rating encompasses ten different security variables that once combined determine an iTrust Rating. Whether you are onboarding potential vendors, benchmarking your vendors across an industry, or are just managing ongoing vendor risk and compliance, an iTrust rating can be used to help monitor and assess a third-party’s real-time security risk.
How is the data collected and how is an iTrust Rating determined?
iTrust data is collected in a non-intrusive manner as iTrust will never enter a network without permission. iTrust uses information gathered from public sources as well as information gathered from the dark-web. iTrust also gathers data from its advanced network of over 53,000 contributors that are monitoring and assessing over 10,000,000 daily threats.
Why use iTrust?
iTrust provides cybersecurity risk ratings and risk intelligence to help businesses build trusted relationships with their vendors, partners, and suppliers. iTrust collects and analyzes third-party risk metrics using machine learning to deliver 360° vendor security and compliance visibility.
iTrust provides:
• Panoramic view of cyber risks – inside, outside, and independent ratings
• Automated continuous compliance monitoring and alerting
• Identify network vulnerabilities and receive alerts in real-time
• Insight into what hackers know about you
• Track breaches and remediation responses
VENDOR RISK MANAGEMENT
Cybersecurity risk ratings across your portfolio of vendors.
BENCHMARKING
Track and measure your security investments.
CYBER INSURANCE
Accelerate underwriting and close more sales with low risk, high yield clients.
MERGERS AND ACQUISITIONS
Accelerate cybersecurity due diligence on merger and acquisition targets.
